Ever wondered why so many companies get hacked? It’s all about the holes in their digital defenses, known as network vulnerabilities.
This article is your go-to guide to understand how these weaknesses invite trouble, like data breaches, and what we can do about it. In simple words, we’re going to explore how keeping our network safe is like locking our doors at night – essential for peace of mind.
Stick around, and you’ll learn how to spot and fix these digital cracks before they become big problems.
Data Breaches and Network Vulnerabilities
Before we engage in disassembling and understanding their symbiosis, it’s crucial to know the bricks that make up this cyber-empire.
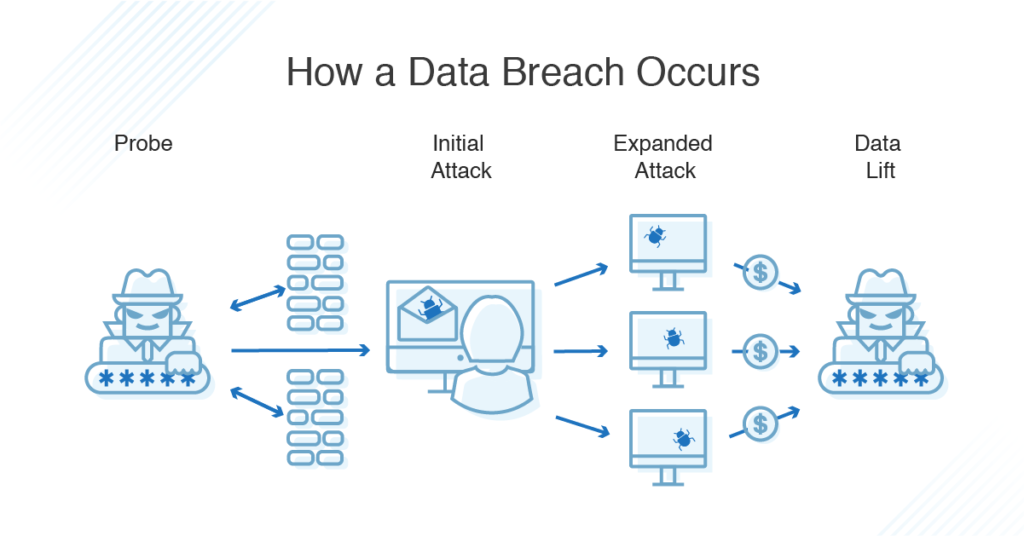
Data Breaches occur when unauthorized persons gain access to a system or database, where sensitive information is housed. Think of them as stealthy thieves that rob you blind without you even knowing they’ve been at work.
On the other side of the coin are Network Vulnerabilities-or as I like to call them, the unlocked doors and open windows of the internet. Weak spots in a network’s defence system invite trouble.
Peeling Back the Layers
To avoid these cyberquakes, we have to start at the roots. Data breaches can be caused by multiple factors. From amateur coding mistakes to sophisticated social engineering, there’s always a chink in the digital armor if you look long and hard enough.
Human Error
Human Error is the oldest and most common reason for a breach. A misplaced decimal point in a line of code or an unintentional email to the wrong person can set off a catastrophic domino effect.
Lack of Cybersecurity Measures
The lack of cybersecurity measures is akin to patrolling the streets without a badge. Without the proper protocols and technologies in place, any cyber-sleuth can waltz into your network and take what they wish.
If persistent vulnerabilities are detected, you should look for experts that can help mitigate the problem. For example, click for cybersecurity in Charlotte to address network security management effectively.
Malware and Phishing Attacks
Malware and Phishing attacks are the assassins in the shadows. They don’t just stumble into your network; they are sent, intentionally and malevolent, with a clear mission to execute.
Proactive Measures
Prevention is the ultimate goal for data security. Here’s how you can start making your castle impenetrable.
Security Best Practices
Implementing a myriad of security practices, from strong password policies to multi-factor authentication (MFA), acts as a much-needed barrier against threats. Regularly updating and patching systems ensures that you’re not leaving any doors open for cyber miscreants.
Employee Education
Your employees are the gatekeepers, and education is their armor. Regular training about the latest threats and the importance of your data security policies can make a significant difference. After all, cyber hygiene is as important as physical hygiene in today’s digital era.
Audits and Updates
Cyber threats evolve at a blistering pace, and so must your defenses. Regular audits to identify and rectify vulnerabilities is part of the ongoing maintenance that’s vital for data security.
The Ultimate Cyber Resilience
In wrapping up, think of countering network vulnerabilities as your digital hygiene routine. It’s not about being perfect; it’s about being smart and staying one step ahead.
By understanding and fixing these weak spots, we can enjoy the internet’s vast opportunities without fear. Remember, a safer digital world begins with us taking action against network attacks.
Was this article helpful to you? If so, make sure to check out our blog for more useful information and resources.













Leave a comment